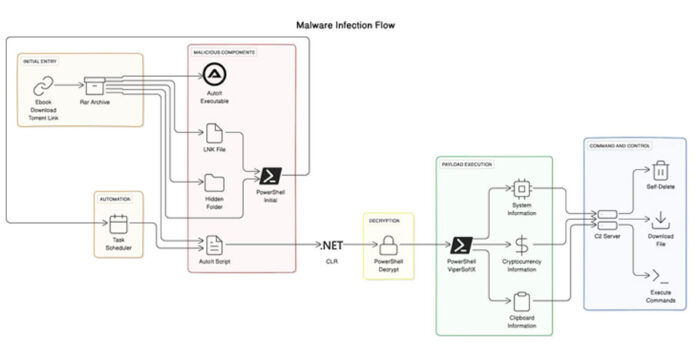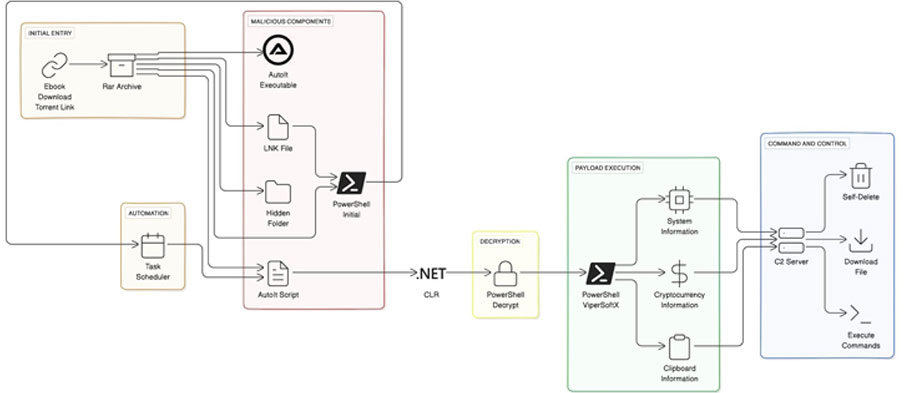
The sophisticated malware known as ViperSoftX has been observed being distributed as eBooks over torrents.
“A notable aspect of the current variant of ViperSoftX is that it uses the Common Language Runtime (CLR) to dynamically load and run PowerShell commands, thereby creating a PowerShell environment within AutoIt for operations,” Trellix security researchers Mathanraj Thangaraju and Sijo Jacob explained.
“By utilizing CLR, ViperSoftX can seamlessly integrate PowerShell functionality, allowing it to execute malicious functions while evading detection mechanisms that might otherwise flag standalone PowerShell activity.”
Initially detected by Fortinet in 2020, ViperSoftX is known for its ability to exfiltrate sensitive information from compromised Windows hosts. Over the years, the malware has evolved, showcasing continuous innovation in its tactics to remain stealthy and circumvent defenses.
This is exemplified by the increased complexity and adoption of advanced anti-analysis techniques such as byte remapping and web browser communication blocking, as documented by Trend Micro in April 2023.
As recently as May 2024, malicious campaigns have leveraged ViperSoftX to distribute Quasar RAT and another information stealer named TesseractStealer.
Attack chains propagating the malware often employ cracked software and torrent sites, but the use of eBook lures is a newly observed approach. The supposed eBook RAR archive file contains a hidden folder and a deceptive Windows shortcut file that appears to be a benign document.
Executing the shortcut file initiates a multi-stage infection sequence that begins with the extraction of PowerShell code, which unhides the concealed folder and sets up persistence on the system. This launches an AutoIt script that interacts with the .NET CLR framework to decrypt and run a secondary PowerShell script, which is ViperSoftX.
“AutoIt does not by default support the .NET Common Language Runtime (CLR),” the researchers noted. “However, the language’s user-defined functions (UDF) offer a gateway to the CLR library, granting malicious actors access to PowerShell’s formidable capabilities.”
ViperSoftX harvests system information, scans for cryptocurrency wallets via browser extensions, captures clipboard contents, and dynamically downloads and runs additional payloads and commands based on responses from a remote server. It also includes self-deletion mechanisms to evade detection.
“One of the hallmark features of ViperSoftX is its adept use of the Common Language Runtime (CLR) to orchestrate PowerShell operations within the AutoIt environment,” the researchers said. “This integration enables seamless execution of malicious functions while evading detection mechanisms that would typically flag standalone PowerShell activity.”
“Furthermore, ViperSoftX’s ability to patch the Antimalware Scan Interface (AMSI) before executing PowerShell scripts underscores its determination to circumvent traditional security measures.”