The JavaScript downloader malware known as SocGholish (also referred to as FakeUpdates) is being used to deliver a remote access trojan (RAT) called AsyncRAT, as well as a legitimate open-source project known as BOINC.
BOINC, which stands for Berkeley Open Infrastructure for Network Computing, is an open-source “volunteer computing” platform developed by the University of California. It is designed to perform large-scale, distributed high-throughput computing using the resources of home computers with the BOINC app installed.
“This platform functions similarly to a cryptocurrency miner by utilizing computer resources for computational work, and it incentivizes users with Gridcoin, a cryptocurrency designed for this purpose,” said Huntress researchers Matt Anderson, Alden Schmidt, and Greg Linares in their report last week.
These malicious setups connect to an actor-controlled domain, such as “rosettahome[.]cn” or “rosettahome[.]top,” serving as a command-and-control (C2) server to gather host data, transmit payloads, and issue further commands. As of July 15, there were 10,032 clients connected to these domains.
While Huntress has not observed any subsequent activities or tasks being executed by the infected hosts, they speculate that these connections could be sold as initial access vectors for other attackers, potentially facilitating ransomware attacks.
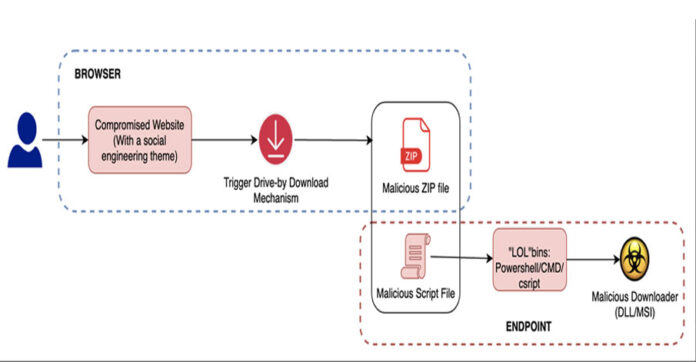
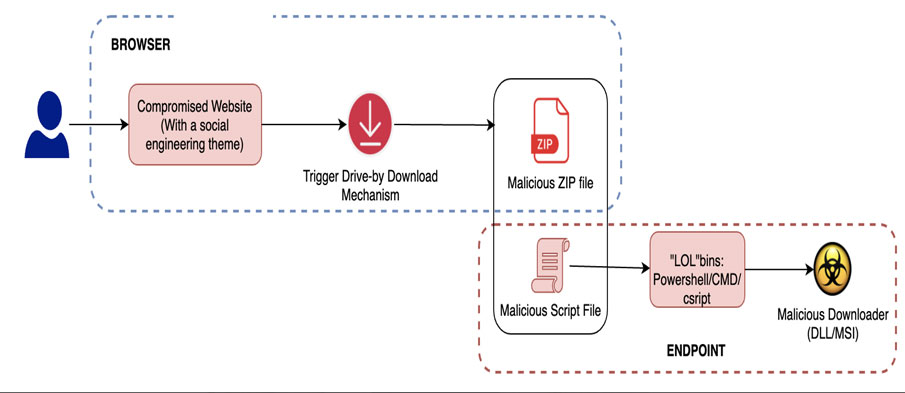
SocGholish attacks typically start when users visit compromised websites, where they are prompted to download a fake browser update. This action triggers the download of additional payloads to the infected machines.
The JavaScript downloader initiates two separate chains: one leading to the deployment of a fileless variant of AsyncRAT and the other to the installation of BOINC.
The BOINC app is disguised as “SecurityHealthService.exe” or “trustedinstaller.exe” to avoid detection and uses a PowerShell script to establish persistence via a scheduled task.
Project maintainers are aware of this misuse and are investigating ways to counteract the malware. Evidence of its abuse has been traced back to at least June 26, 2024.
“The exact motivation behind installing this software on infected hosts remains unclear,” the researchers noted.
“Infected clients connecting to malicious BOINC servers pose a significant risk, as threat actors could exploit these connections to execute various malicious commands or software on the host, escalating privileges or spreading through a network to compromise an entire domain.”
This development comes as Check Point reports on the use of compiled V8 JavaScript by malware authors to evade static detections and hide remote access trojans, stealers, loaders, cryptocurrency miners, wipers, and ransomware.
“In the ongoing struggle between security experts and threat actors, malware developers continually invent new methods to conceal their attacks,” said security researcher Moshe Marelus. “The adoption of V8 is unsurprising, given its widespread use in software development and its resistance to analysis.”