Cybersecurity researchers have unveiled an adware module that falsely claims to block ads and malicious websites while covertly deploying a kernel driver component. This component allows attackers to execute arbitrary code with elevated permissions on Windows systems.
Named HotPage, the malware is identified by its installer (“HotPage.exe”), according to recent findings from ESET, which discovered the malware at the end of 2023.
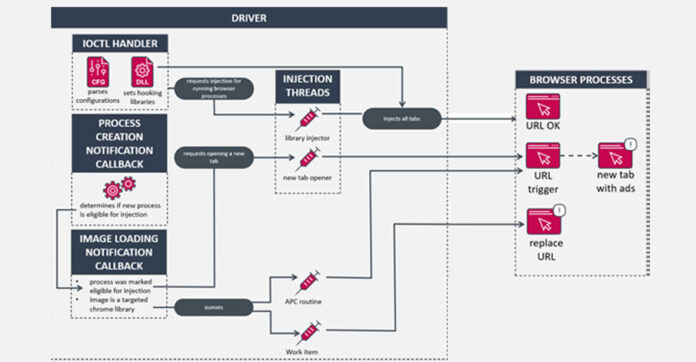
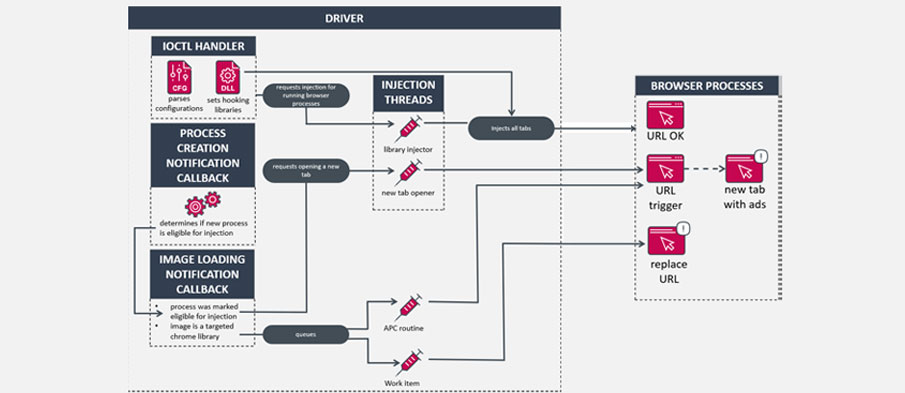
“The installer deploys a driver capable of injecting code into remote processes and two libraries that intercept and manipulate browsers’ network traffic,” ESET researcher Romain Dumont detailed in a technical analysis released today.
“The malware can alter or replace the contents of a requested page, redirect the user to another page, or open a new page in a new tab under certain conditions.”
In addition to using its browser traffic interception and filtering capabilities to display game-related ads, HotPage is designed to harvest and exfiltrate system information to a remote server operated by a Chinese company named Hubei Dunwang Network Technology Co., Ltd
This is achieved through a driver whose main purpose is to inject the libraries into browser applications and modify their execution flow to change the URL being accessed or to set the homepage of a new web browser instance to a specific URL specified in a configuration.
Moreover, the lack of access control lists (ACLs) for the driver means that an attacker with a non-privileged account could exploit it to gain elevated privileges and execute code as the NT AUTHORITY\System account.
“This kernel component unintentionally leaves the door open for other threats to run code at the highest privilege level available in the Windows operating system: the System account,” Dumont explained. “Due to improper access restrictions to this kernel component, any processes can communicate with it and use its code injection capability to target any non-protected processes.”
HotPage Adware
Although the exact distribution method of the installer is unknown, evidence from the Slovakian cybersecurity firm indicates that it has been promoted as a security solution for internet cafés, purportedly enhancing users’ browsing experience by blocking ads.
Notably, the embedded driver is signed by Microsoft. The Chinese company appears to have navigated Microsoft’s driver code signing requirements and obtained an Extended Verification (EV) certificate. This certificate was removed from the Windows Server Catalog as of May 1, 2024.
Microsoft requires kernel-mode drivers to be digitally signed to be loaded by the Windows operating system, a defense mechanism to protect against malicious drivers that could undermine security controls and interfere with system processes.
However, last July, Cisco Talos revealed how native Chinese-speaking threat actors exploited a Microsoft Windows policy loophole to forge signatures on kernel-mode drivers.
“The analysis of this seemingly generic piece of malware has shown that adware developers are still willing to go to great lengths to achieve their goals,” Dumont commented. “Not only did they develop a kernel component with extensive techniques to manipulate processes, but they also navigated Microsoft’s requirements to obtain a code-signing certificate for their driver component.”