The China-linked threat actor known as Evasive Panda compromised an unnamed internet service provider (ISP) to push malicious software updates to target companies in mid-2023, demonstrating a new level of sophistication for the group.
Evasive Panda, also known as Bronze Highland, Daggerfly, and StormBamboo, is a cyber espionage group active since at least 2012. They have utilized backdoors such as MgBot (also known as POCOSTICK) and Nightdoor (also known as NetMM and Suzafk) to collect sensitive information.
Recently, the group has been linked to a macOS malware strain called MACMA, which has been observed in the wild since 2021.
“StormBamboo is a highly skilled and aggressive threat actor who compromises third parties (in this case, an ISP) to breach intended targets,” Volexity reported last week.
“The variety of malware used in various campaigns by this threat actor indicates significant effort, with actively supported payloads for macOS, Windows, and network appliances.”
Reports from ESET and Symantec over the past two years have documented Evasive Panda’s use of MgBot and their history of orchestrating watering hole and supply chain attacks targeting Tibetan users. The group also targeted an international non-governmental organization (NGO) in Mainland China, delivering MgBot via update channels of legitimate applications like Tencent QQ.
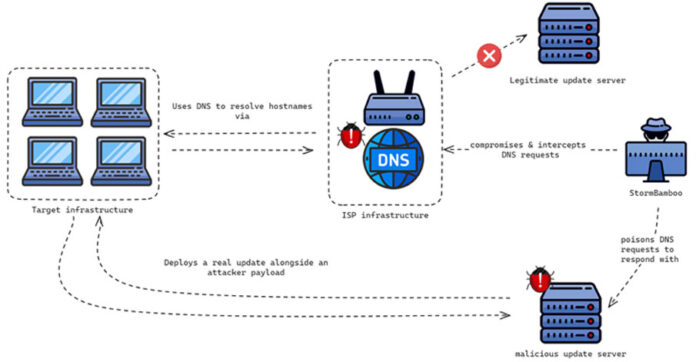
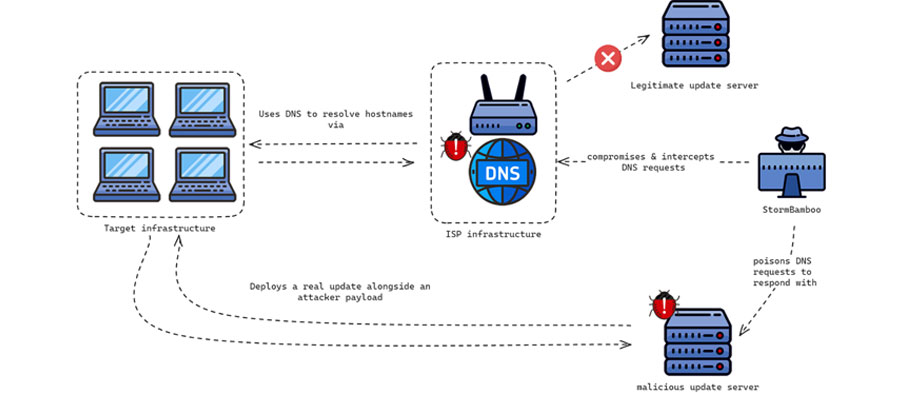
Speculation suggested that the trojanized updates resulted from either a supply chain compromise of Tencent QQ’s update servers or an adversary-in-the-middle (AitM) attack. Volexity’s analysis confirms the latter, attributing it to a DNS poisoning attack at the ISP level.
The threat actor altered DNS query responses for specific domains tied to automatic software update mechanisms, targeting software using insecure update mechanisms (e.g., HTTP) or lacking adequate integrity checks of the installers.
“StormBamboo poisoned DNS requests to deploy malware via an HTTP automatic update mechanism and poison responses for legitimate hostnames used as second-stage command-and-control (C2) servers,” explained researchers Ankur Saini, Paul Rascagneres, Steven Adair, and Thomas Lancaster.
The attack chains exploited insecure update mechanisms to deliver either MgBot or MACMA, depending on the operating system. Volexity notified the affected ISP to address the DNS poisoning attack.
One instance involved deploying a Google Chrome extension on the victim’s macOS device by modifying the Secure Preferences file. The browser add-on posed as a tool for loading pages in Internet Explorer compatibility mode but primarily aimed to exfiltrate browser cookies to a Google Drive account controlled by the adversary.
“The attacker can intercept DNS requests and poison them with malicious IP addresses, using this technique to abuse automatic update mechanisms that use HTTP rather than HTTPS,” the researchers concluded.