Cybersecurity researchers have uncovered a new phishing campaign that exploits Google Drawings and shortened links created through WhatsApp to bypass detection and lure users into clicking on malicious links aimed at stealing sensitive information.
“The attackers cleverly utilized some of the most trusted websites in the tech industry to construct this threat, including Google and WhatsApp for hosting attack components and a fake Amazon site to collect the victim’s information,” explained Ashwin Vamshi, a researcher at Menlo Security. “This attack is a prime example of a Living Off Trusted Sites (LoTS) threat.”
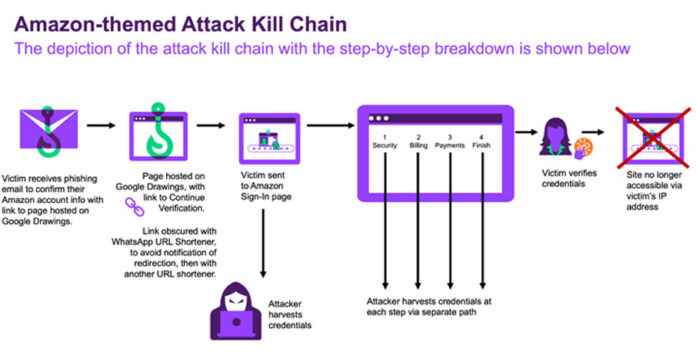
The attack begins with a phishing email that directs recipients to a graphic resembling an Amazon account verification link. This graphic is hosted on Google Drawings, likely to avoid detection by security systems.
Using legitimate services offers significant advantages to attackers, as these platforms provide a low-cost and discreet method of communication within networks, making them less likely to be flagged by security tools or firewalls.
“One reason Google Drawings is particularly appealing at the start of the attack is that it allows users, in this case, the attacker, to embed links within graphics,” Vamshi noted. “These links can easily go unnoticed by users, especially if they feel a sense of urgency about a potential threat to their Amazon account.”
When users click on the verification link, they are redirected to a fake Amazon login page. The URL of this page is obscured by two successive URL shorteners—WhatsApp (“l.wl[.]co”) and qrco[.]de—to further evade security checks.
The fake page is designed to steal credentials, personal information, and credit card details. Once the victim’s credentials are captured, they are redirected to the actual Amazon login page. Additionally, the phishing site becomes inaccessible from the same IP address after the credentials are submitted.
This revelation comes as researchers have identified a vulnerability in Microsoft 365’s anti-phishing mechanisms, which could be exploited to increase the likelihood of users opening phishing emails.
The technique involves using CSS manipulation to hide the “First Contact Safety Tip,” a warning that alerts users when they receive an email from an unknown sender. Microsoft has acknowledged the issue but has yet to release a fix.
“The First Contact Safety Tip is added to the body of an HTML email, which means its display can be altered using CSS style tags,” stated the Austrian cybersecurity firm Certitude. “We can even take this further by spoofing the icons that Microsoft Outlook adds to emails that are encrypted and/or signed.”